App cloning is a serious threat that allows attackers to duplicate popular mobile applications and distribute them as fake versions. These cloned apps often contain malicious code, collect sensitive data, or manipulate transactions without the user’s knowledge.
Anti-reverse engineering is the strongest defense against this threat because it prevents attackers from understanding the app’s internal structure. Mobile app defense requires a proactive approach to protect the app from being copied or misused.
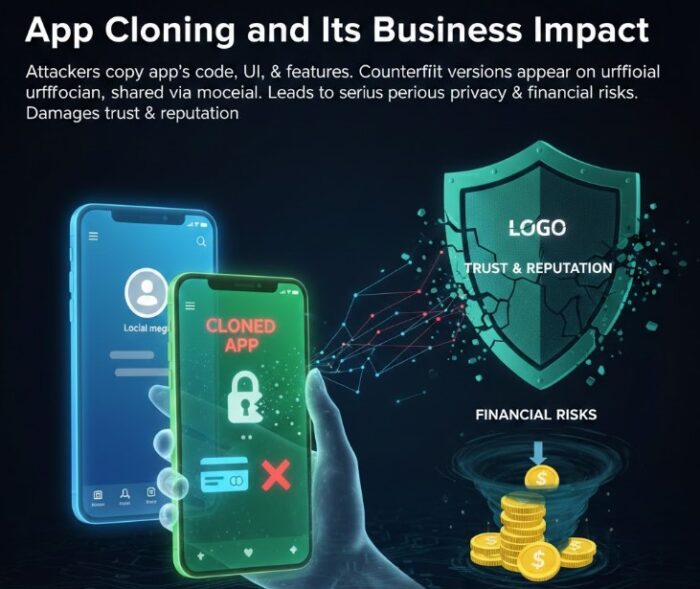
App Cloning and Its Business Impact
App cloning happens when attackers copy an app’s code, UI, and features to create a counterfeit version. These fake apps can appear on unofficial app stores or be shared through social media links, making it hard for users to identify the original app. When cloned apps collect user credentials or payment information, it leads to serious privacy and financial risks. Users often report these issues to the original company, damaging trust and reputation.
- User Data Theft
Cloned apps are often designed to collect sensitive user data such as login credentials, bank details, and personal information. Users assume they are using a legitimate app, making them less cautious. Once data is stolen, attackers can use it for identity theft, fraud, or resale on dark web markets. The original brand is then blamed for the breach, damaging its reputation. - Financial Fraud
Fake apps can redirect payments, create fake subscriptions, or manipulate in-app purchases. Users may unknowingly pay for services that never exist, leading to financial loss. This also reduces the revenue of the authentic app, as users stop trusting the platform. Businesses must invest in security to prevent such financial risks. - Malware Distribution
Cloned apps often include malware or spyware that damages devices and compromises security. Malware can also turn devices into bots for larger cyber attacks. The presence of malware affects user trust and can lead to legal consequences for the brand. Strong security prevents these threats from spreading.
Reverse Engineering Enables Cloning
Reverse engineering allows attackers to break down the app’s code and understand its logic, APIs, and security features. This process helps them replicate the app’s functionality and create a fake version. Attackers use reverse engineering to identify weak points in the app, such as exposed APIs or insecure logic. This information makes it easier to bypass security controls. A strong anti-reverse engineering approach is necessary for effective mobile app defense and the prevention of cloning attacks.
- Decompiling Code
Decompiling converts the app’s binary files into readable source code, allowing attackers to analyze the app. This reveals the app’s logic, algorithms, and structure. Once the code is readable, attackers can replicate features or remove security checks. It also helps them identify sensitive functions to exploit. - Static Analysis
Static analysis involves examining the app’s structure without running it. Attackers can explore the code, resources, and libraries to find vulnerabilities. This helps them create a detailed map of the app’s internal flow. It also reveals hidden features and sensitive data paths. - Dynamic Analysis
Dynamic analysis monitors the app while it runs to understand its behavior. Attackers use tools to inspect runtime data, API calls, and app actions. This reveals how the app interacts with servers and handles security checks.
Anti-Reverse Engineering as a Primary Defense
Anti-reverse engineering techniques are designed to prevent attackers from understanding or modifying the app’s code. This makes cloning highly difficult and costly. These techniques protect the app’s logic, algorithms, and sensitive modules from being extracted or reused.
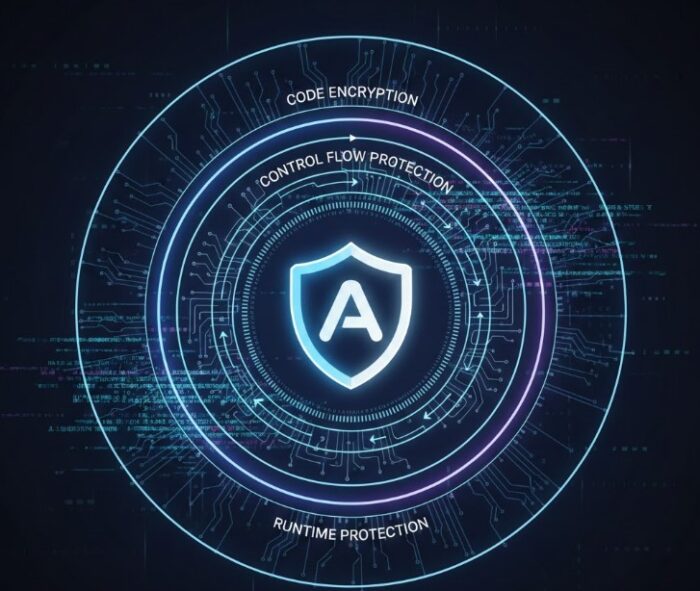
- Code Encryption
Code encryption hides the app’s core logic by transforming it into an unreadable form. Attackers cannot easily access or analyze encrypted code. This prevents them from extracting sensitive algorithms or features. - Runtime Protection
Runtime protection safeguards the app while it is running, preventing real-time analysis and manipulation. Attackers cannot easily observe or modify app behavior during execution. - Control Flow Protection
Control flow protection alters the app’s execution path, making it hard to follow the logic. Attackers struggle to understand the real flow of the app.
Code Obfuscation for Increased Security
Code obfuscation makes the app’s code confusing and hard to interpret without changing its functionality. It hides the real purpose of functions and variables. Obfuscation prevents attackers from understanding the app’s logic even after decompiling.
- Renaming Variables and Methods
Obfuscation replaces meaningful names with random characters, making it difficult to understand the code’s purpose. Attackers cannot identify which methods are critical.
This increases the time needed for analysis and reduces the chance of successful cloning. It also prevents attackers from quickly locating sensitive modules. - Control Flow Obfuscation
This technique modifies the logical flow of the app, making it appear confusing. Attackers cannot easily follow the execution path. It creates false branches and loops that mislead analysis tools. The complexity increases the cost of reverse engineering. - String Encryption
Sensitive text, such as API keys, URLs, and tokens are encrypted. Attackers cannot extract these values even after decompiling. This prevents unauthorized access to backend systems. It protects the app’s authentication and communication channels.
Anti-Tampering for App Integrity
Anti-tampering ensures the app detects unauthorized changes to its code or resources. When tampering is detected, the app can block execution or alert security teams. This prevents attackers from modifying the app to bypass security checks or inject malicious code.
- Integrity Checks
Integrity checks verify the app’s checksum or signature at runtime. Any changes trigger protective actions. Attackers cannot modify the app without being detected. It prevents cloned versions from running or accessing services. - Debug Detection
Detects if the app is being analyzed with debugging tools. This prevents attackers from bypassing security checks during runtime. Debugging tools are commonly used for reverse engineering. - Root/Jailbreak Detection
Detects if the device is compromised. Attackers often use rooted or jailbroken devices to bypass security. Blocking these devices reduces cloning risks.
Conclusion
Anti-reverse engineering is a vital defense against app cloning. It makes the app difficult to analyze, preventing attackers from understanding the code and replicating it. When combined with anti-tampering, RASP, secure key management, and monitoring, it creates a powerful shield against cloning threats and fraud.
For businesses seeking advanced protection, platforms such as doverunner offers comprehensive app security solutions that strengthen mobile app defense through anti-reverse engineering, runtime protection, and threat monitoring. With its strong focus on app integrity and security, DoveRunner helps organizations prevent cloning and maintain user trust.